T-Mobile January 2023 Hack
On January 19th, 2023 T-Mobile disclosed a new data breach when a bad actor stole the personal information of 37 million customer accounts. While the company claims that no social security or account information was included in the hack, identifiable data including: name, billing address, email, and phone number, was found to have been taken. This is the eighth T-Mobile data breach since 2018.
Today, most online web services use APIs to provide content to their applications or external partners. An API is an interface to allow services or applications to communicate with another service. Typically, APIs require a valid authentication token to return data. T-Mobile did not specify the manner in which its own public facing API was breached, but data was returned to a bad actor nonetheless.
Attacks that Exploit APIs
Credential stuffing
One of the most common attacks is the Credential Stuffing Attack. It is a form of brute force attack in which criminals use stolen usernames and passwords to access user accounts in other systems. Public APIs often issue authentication tokens to valid, authenticated user accounts and leverage third-party authentication services to verify the identity.
Stolen authorization tokens
In a similar scenario, valid authorization tokens can be taken from valid users through man-in-the-middle, phishing, and scraping attacks. Last year, GitHub security reported that a threat actor had gained access to private repositories using stolen OAuth credentials.
SQL injection attacks
In a SQL Injection attack, an attacker can execute queries on a database remotely through a request to the API. This attack is still common and is likely the most dangerous.
Excessive data exposure
APIs should only return data which is relevant to the consumer. Often, an API will contain endpoints for general and sensitive data in the same interface. Using location data that its API exposed unnecessarily, an application called 3fun exposed dating preferences in users at the White House, Congress, and other Government institutions. By pinpointing the exact users and their birthdate, personal photos were hacked.
Why are APIs Vulnerable?
In an article published by SCMedia:
- 95% of surveyed organizations have experienced an API security incident in the past 12 months.
- 34% have no API security strategy in place.
- API attacks rose 681% in 12 months.
- 83% of respondents are not very confident that their API inventory is safe.
The truth of the matter is that many APIs are vulnerable because they are poorly designed. However, for those that are vulnerable, the time spent rewriting or upgrading them is cost-prohibitive. Even then, an API that is following best practices with excellent design could still be breached due to human error.
What Can Be Done To Protect APIs?
API hardening with Eclypses MTE
At Eclypses, the Applied Technology team works with customers to confound potential hackers by eliminating many of the ways they might attack an API.
Unique one-to-one pairings
The Eclypses MTE is a simple toolkit that allows client and server to form very unique pairings with one another. A stolen API Key has no value when the hacker has no ability to communicate with the server.
Encoded response payloads
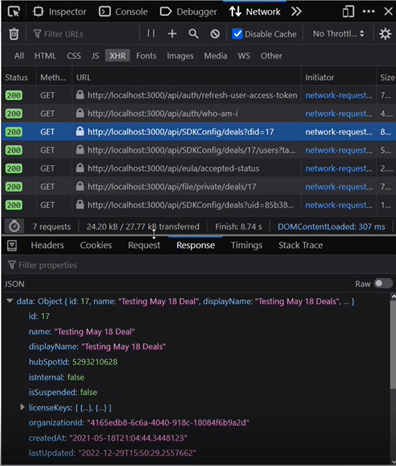
Modern best practices say that TLS is safe. When it comes to excessive data exposure, TLS does nothing to keep bad actors from inspecting data returned from APIs which may include IDs and other sensitive values.
Example:
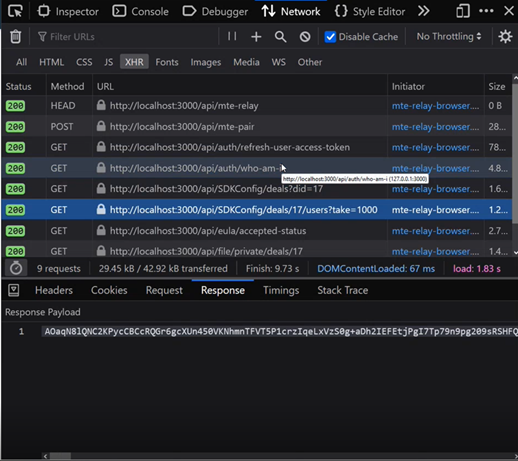
Bolt-on Protection
In the previous example, Eclypses MTE was added to an unsecure API in minutes without removing TLS, network throttling, authentication, or any other security measure. MTE vastly improved the API’s defense against credential stuffing, injection attacks, and the exposure of excessive (or any) data. Combined with the Eclypses Cryptographic module and the patented, award-winning data replacement technology of Eclypses MTE, a simple API can become much more resilient to attacks without the need for re-architecting.
Dan Lemoine, Sr. Director of Operations at Eclypses, recently worked with a customer who successfully integrated MTE into their platform and noted, “This customer went so far as to hire a security expert contractor to test (hack) the MTE secured platform immediately following the integration of MTE due to the sensitive data that needed to be protected. The contractor was allowed onto the customer’s network, where hacking attempts were executed, utilizing free and paid professional hacking utilities. The ‘hacker’ was eventually able to see the MTE encoded ‘data’ being passed over the network and grew frustrated not being able to crack and read the encoded data being passed.”
To sum up, adding Eclypses MTE to a vulnerable public API can harden its endpoints instead of a lengthy, expensive redesign. Implementation is scalable with low effort while adding redundancy and data-in-transit security. When it comes to risk and the reputation of a company, an insignificant public endpoint can destroy years’ worth of goodwill. Eclypses MTE can be added to confound and secure the endpoint quickly and inexpensively to mitigate the risk.
Written by: Joe Jeanjaquet, Senior Director of Engineering at Eclypses
For more information, please contact the Eclypses team.


