
Just about everyone uses a smartphone today – for entertainment, sending messages, taking pictures, storing information, sending money, and of course, talking on the phone. With so much of our daily lives relying on one device, we wouldn’t want someone to gain access to our sensitive information.
What is SIM Swapping?
SIM stands for subscriber identity module and SIM swapping (also referred to as SIM jacking, SIM splitting, or SIM hijacking) is when a person convinces your mobile carrier to port your phone number over to their SIM card. By doing this, the hacker can easily access your most sensitive accounts by completing text-based two-factor authentication checks.
What are Cloning Attacks?
In cloning attacks, the goal is the same as with SIM Swapping, however, the attack is more sophisticated. As we know, cloning means duplicating the original. Hackers use smart card copying software in order to create a copy of the real SIM card, which gives the hacker access to the victim’s international mobile subscriber identity (IMSI) and master encryption key.
What Do Hackers Want from Your SIM?
When hacking your SIM card, hackers are interested in account information, financial information, and PII, which stands for personally identifiable information. According to Cyware Social, “Nowadays, many large service providers prefer sending SMS messages to their customers as a second factor of authentication for their online accounts. With a hacked SIM card, your online accounts can thus be compromised easily.”
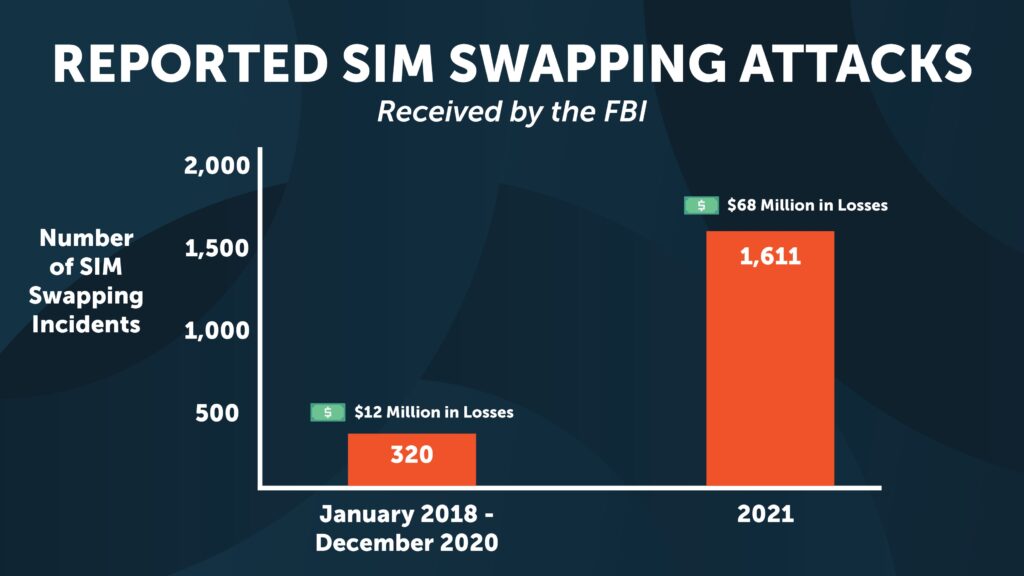
Reported SIM Swapping Attacks Reported by the FBI
In 2022, the FBI issued a new alert regarding SIM swapping attacks, as the number of reported cases has dramatically increased. From January 2018 to December 2020, the FBI reported that they received 320 complaints related to SIM swapping attacks, and of those attacks approximately $12 million in losses. Alarmingly, in 2021 the FBI reported 1,611 incidents received related to SIM Swapping, and of those attacks approximately more than $68 million in losses.
How MTE Technology Prevents SIM Swapping and Cloning Attacks
In order to prevent successful SIM Swapping, Eclypses MTE Technology verifies each endpoint connection by establishing a unique MTE relationship with the physical device and the server which it is trying to communicate with. An example of how this works could be during the registration of an application. While the user is setting up the app, signing in, and registering their device, the app could have the user move a cursor around the screen with their finger. By having the user move their finger around the screen in a random motion, collecting the coordinates of the movements, and then adding them all together – a random, non-replicable, number is created. This number can then be fed into the instantiation of the MTE as part of the seed value. By having a multipart seed value and this random number as part of that value, it makes it nearly impossible for a cybercriminal to compromise.
The random number will be shared between that specific instance of the app and server setting up a unique relationship between the two. This number is single-use and will be instantly obsolete after MTE instantiation is complete. This eliminates the ability for someone to discover the value and compromise the communication. With this process in place, the user could give a cybercriminal their username, password, and two-factor authentication code and the criminal would still not be able to log into an app from another device.
Interested in learning more about Eclypses MTE technology? Reach out to our team today.
Sources: CywareSocial, Mozilla, FBI


