
Whoever said that efficiency is maximized through simplicity needed to be more familiar with microservices. Compared to the monolithic applications of the past, microservices can make our applications far more capable, agile, powerful, and unfortunately, complex. As operations are distributed through dozens or hundreds of entry points, developers can deliver application functionality rapidly and reliably. On the other hand, more nodes mean more points of vulnerability and its own unique set of security requirements.
Benefits of Microservices
Productivity and Speed
Microservices can improve development by separating common functions into their own services. For instance, if multiple teams need to add authorization to their application, they could:
- All add their own business logic to their application which replicates code or creates multiple unique processes. This makes scalability impossible and is very inefficient.
- The enterprise could create an authorization microservice to provide a common authorization capability to every application in a distributed system. Everyone uses the same authentication schema, and it can scale as needed.
Orchestration with Containers
Container solutions like Docker and orchestration frameworks like Kubernetes are not new technologies, but are quickly gaining traction with businesses looking to become scalable and agile. In a global survey published by Datadog, engineering teams continue to expand their use of containers, and Kubernetes is now used by nearly 50% of organizations in the report.
In the example of an authorization microservice, when containerized, the service can be deployed to any server on-premise or in the cloud at a moment’s notice and easily load-balanced as needed.
Deployment without Disruptions
When precise functions are contained to a single microservice and deployed using a container, updates to architecture components become extremely safe, selective, and specific. When the authorization microservice needs to be updated, a new container is built and deployed seamlessly instead of recompiling a large monolithic application.
Security Concerns
Complexity
The increase in Microservice architecture is not all positive. As a retrospective to Datadog’s survey, Yrieix Garnier, Vice President of Product at Datadog stated, “hand-in-hand with this growth, our research shows an increase in complexity that leads to potential security risks organizations should consider.” The study showed that 50% of container customers were running unsupported versions of Kubernetes, and over 30% were running unsupported versions of containers that contained unpatched vulnerabilities.
Increase in Network Requests
The biggest side effect of the microservice architecture is the sheer number of network requests required to perform operations in an application. A simple function, such as account creation, may require multiple requests to a dozen services to complete the process. With data being passed between these systems being a company’s most valuable asset, protection of the data that moves requires the highest level of protection.
Is TLS Enough?
Successful Man-in-the-Middle (MiTM) attacks gain the trust of communicating parties by impersonating or accessing SSL/TLS keys and certificates. While difficult to fake a trusted Certificate authority in a public website, server administrators often create self-signed “wildcard” certificates on-demand using free tools like OpenSSL. This is quick and easy but does not verify the authenticity of the certificate with a trusted third-party authority. This practice opens the door for malware and malicious software to easily decrypt traffic within the network.
Even when certificates are verified and implemented securely with best practices, modern Public Key Infrastructure is vulnerable to future brute-force or quantum-level attacks. What is truly needed is a stand-alone, quantum resistant, security solution that can be implemented quickly without affecting existing accessibility or functionality.
Eclypses MTE and Data-In-Transit
The Eclypses MTE is an application-level toolkit designed to secure Web, Mobile, IoT, and connected services. The product is embeddable, fast, and future-resistant without affecting other security because it only affects the data as it moves. On the surface, this seems like the perfect solution for protecting data in a microservice environment because data can be replaced with instantly obsolete bytes at the client and obscured from any observer in between.
Eclypses to the Rescue
The engineering team at Eclypses loves solving problems, and the prospect of making implementation as easy as possible is one of its highest priorities. As a result, Eclypses have created a stand-alone, containerized HTTP Proxy middleware to install quickly and seamlessly into a microservice environment. In fact, it has been dutifully protecting Eclypses’ own microservice environment. The container, along with a client-side package for Web and Mobile applications, can secure data produced from a browser or app to its eventual resting place with a consistent level of security validated by NIST. Most importantly, Eclypses MTE does not affect or impede any other network-level security solutions such as monitoring, firewall, and TLS.
Simple – Securing Data from Client Application to the Edge
The simplest implementation of the technology is found in figure 1. While this setup does not secure network traffic between microservices, it does protect from the application to the API Gateway without having to change anything in the existing architecture. Eclypses MTE can secure everything outside the firewall.
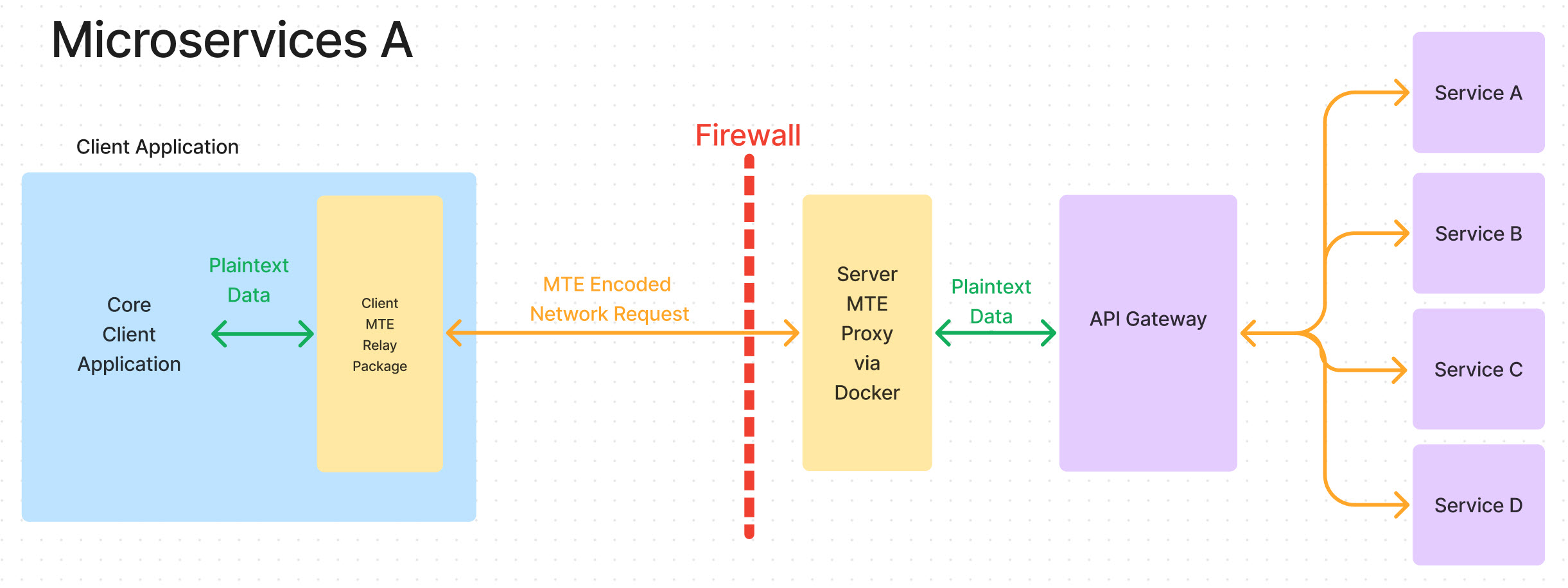
Microservice Security – Securing Data through the API Gateway to the Microservice
In figure 2, Eclypses MTE is still securing data between the application and the endpoint but is now obscuring data from the API gateway as well. In this example, malware will have no ability to decrypt or decipher any data across the network.
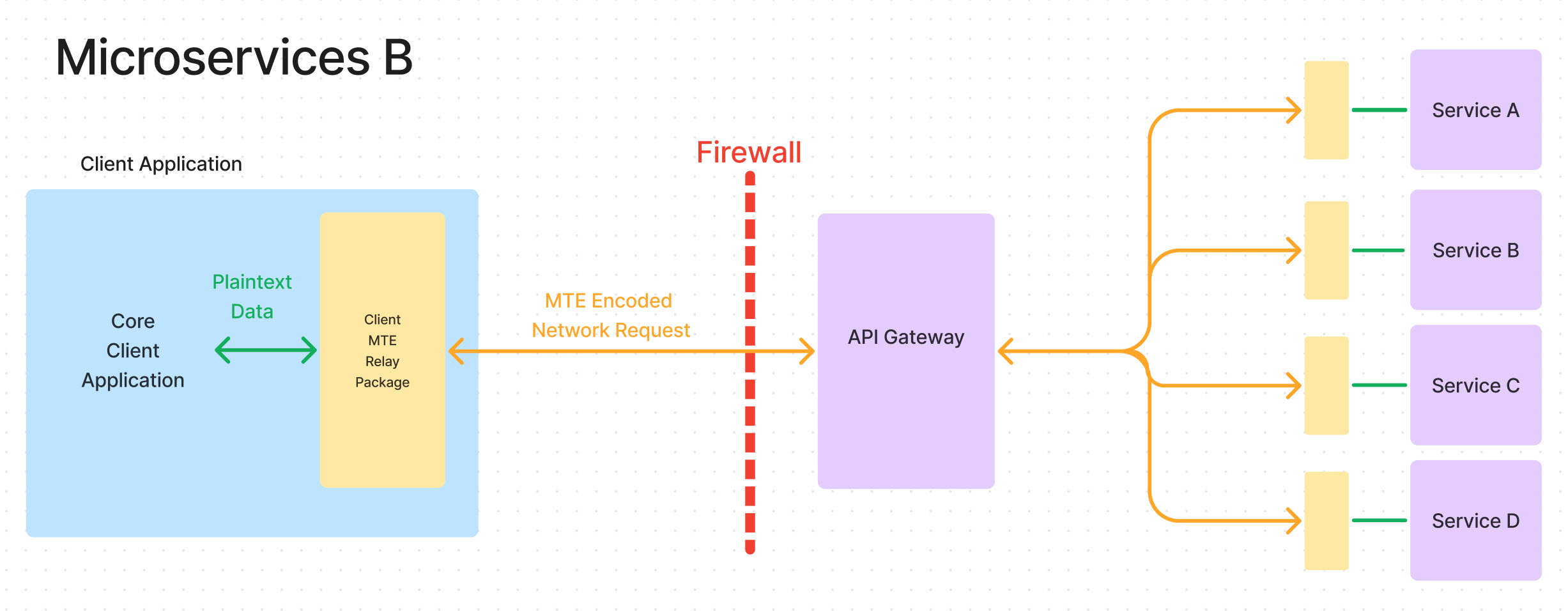
Service to Service / Server to Server
Since the Eclypses container is endlessly scalable, it can be positioned to proxy data between services or servers with its own firewall. This could even be a partner or customer environment that is not controlled by the enterprise. An example of a service-to-service or server-to-server implementation can be found in figure 3.
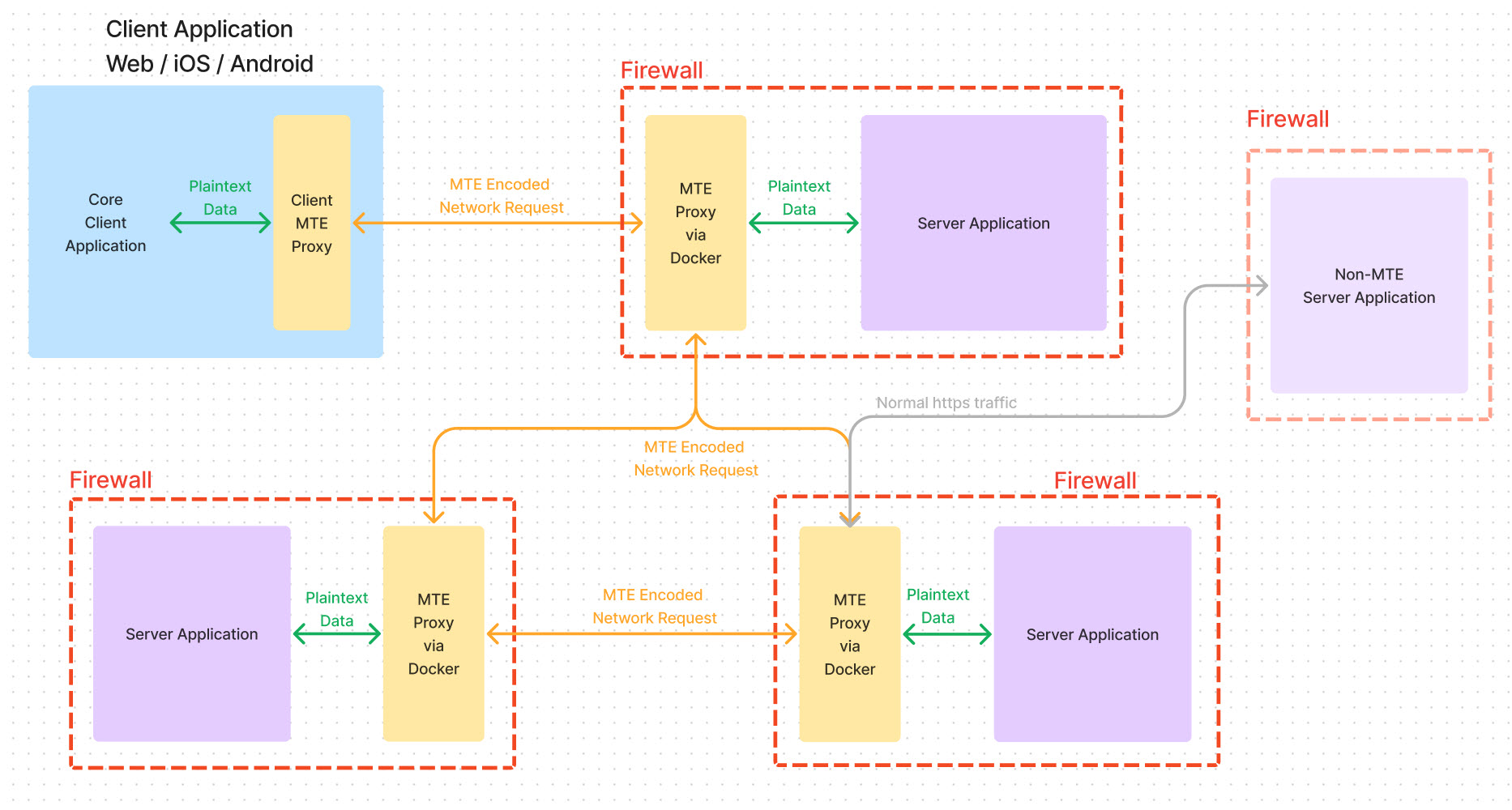
The Future of Microservice Architecture
Truly, scalability and efficiency require agile application architectures and the use of microservices will continue for the foreseeable future. With that in mind, security and data protection are essential to ensure the complex applications powering future businesses are able to be utilized for decades to come. A simple, scalable, future-resistant data protection solution, like Eclypses MTE, will protect against current and future problems caused by the complexity of the architecture.
When containers are running on unsupported software, the data is protected. When malware and malicious MiTM software look to steal your most valuable asset, the data is protected. And when application developers and network engineers cannot afford a costly re-engineering effort to bolster security, Eclypses MTE can be easily implemented at scale to make the data is protected without having to change a single thing.
Written by: Joe Jeanjaquet, Senior Director of Applied Technologies at Eclypses
For more information, please contact us by filling out the form below:


