
What is RSA?
RSA is a cryptography that continues to be prevalent in many technologies and products. RSA is a public-key mechanism for orchestrating secure data transmission and is one of the oldest key exchange algorithms. RSA was revolutionary for its time, but as computing systems have evolved, the strength of RSA has dramatically deteriorated. The attacks on RSA are plentiful and rudimentary for attackers to execute. 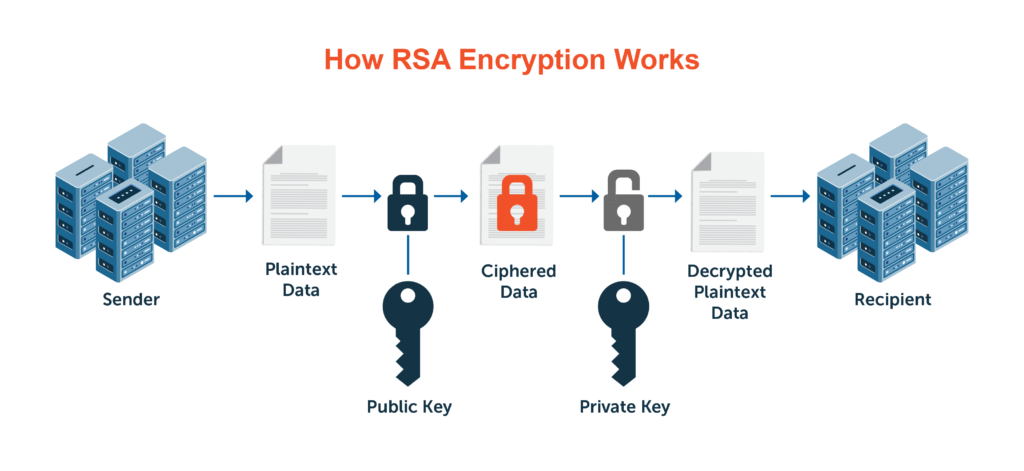
The Challenges RSA Presents
RSA’s base design makes it inherently hard to use, resulting in implementation complications. The user, usually a developer, is left to choose the initialization values of their RSA implementation. Rarely are developers well versed enough in cryptography and the mathematics RSA is built upon to determine adequate values. As a result, the initialization values that are often used lead to little or no security. So, while a developer did their best, all the data being secured by RSA is vulnerable, while the organization that owns the data thinks it is secure.
Problems with the base design of RSA continue deeper into how the algorithm works. If RSA encrypts the same data multiple times, the same result will be produced. This opens RSA to man-in-the-middle attacks such as replay, delay, injection, etc. For this reason, it is recommended that data is padded with random values so that results differ. The problem is that RSA does not handle this padding, so again, it is left up to the developer to choose it and affix it to their data. There are padding schemes to reduce padding errors and make it easier, but some of those have been determined to leak information. This leaked information about the encrypted messages or keys makes data susceptible to vulnerabilities such as forgery attacks and padding oracle attacks, i.e., ROBOT. So again, while the implementor and data owner think they are protecting the data and padding it effectively, the data is left exposable by attackers.
But there are still vulnerabilities even if the user correctly initializes RSA and preps the data. RSA’s public/private key pair creation method is susceptible to factorization attacks. In a factorization attack, an attacker impersonates a key owner and can get the private key for the pairing. This allows attackers to decrypt sensitive data and bypass a system’s security. There are ways to make this more challenging, like using longer keys, but the fact that this hack is possible means that as computers continue to become more powerful, they can compromise longer and longer keys.
While band-aids, like those previously mentioned, make people justify the continued use of RSA, the slight modification of attacks can make them effective again. On top of this, there is a constant stream of new attacks that open holes in RSA, illustrating a fundamental problem with its design. These considerations, plus the ever-nearing accessibility of quantum computing, should be enough to cease using RSA, but that has not happened. Some popular and newly developed software products still use RSA as a fundamental building block in their cybersecurity approaches. This is bad, but hope is not lost for the users of these products. While it is unlikely to make progress by demanding change from software companies, enterprise consumers can instead take control of their data security.
Next Generation Security Solution
By implementing application-layer data security, the insecurities of third-party products become less detrimental. Data security within the enterprise’s environment allows data to be secured before being handed to third-party products, communication protocols, or operating systems. This significantly reduces the need to trust anything out of the enterprise’s control. Eclypses’ MTE technology is a future-oriented cybersecurity technology that can be embedded into any application, allowing the data to be secured at its origin. Data should be protected as soon as possible to reduce the chance of exposure from bad practices or zero days within third-party products, communication protocols, or operating systems. Ultimately, using external software and tools is inevitable, but that doesn’t mean control of data security should be relinquished.
The MTE technology allows enterprises to take back control and protect their data from external factors by adding layers to their data security. MTE is not a “rip-and-replace” technology. It works alongside existing securities to provide a depth of data security previously unseen. MTE aims to create consistent high-strength security regardless of devices or software involved in data transmission. From 8-bit microcontrollers to the most powerful servers, MTE can effectively and consistently secure data and keep it secure even as technological advancements are made in computing.
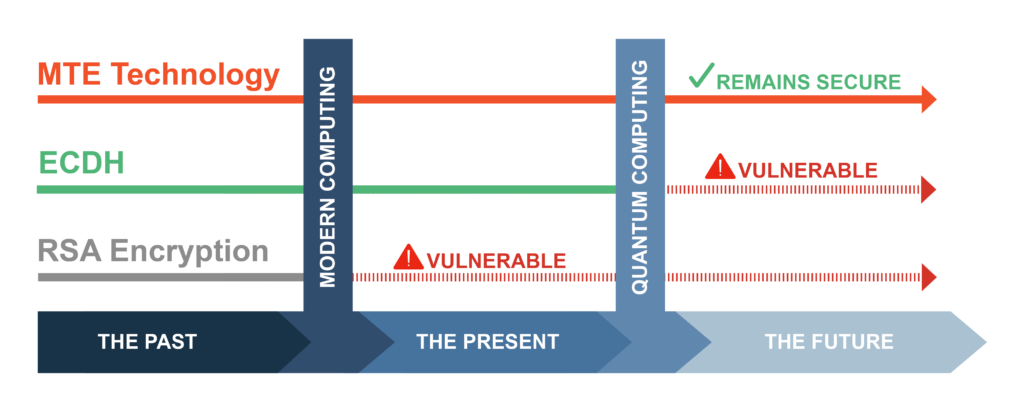
MTE was developed with quantum in mind, providing an alternative way of utilizing industry-standard protocols to randomly obfuscate and replace data instead of encrypting it. This new approach to data security removes most attacks common today and those theorized for the future. RSA’s deficiencies have led to new and more robust key exchanges, such as Elliptic Curve Diffie-Hellman (ECDH), which is excellent. However, ECDH is still not resistant to quantum computing. That insight has led to work on quantum-proof key exchange algorithms such as Kyber, which have their own challenges. The previous front runner in this quantum-proof key exchange race was Supersingular Isogeny Diffie-Hellman (SIDH), determined insecure after a simple attack was identified. These quantum key exchanges have years before they are fully fleshed out, and even then, it is unclear if they will be resistant to both classical and quantum computing attacks or only resistant to quantum. Implementing MTE into enterprise applications makes concerns with RSA, ECDH, quantum computing, or any other external vulnerability less detrimental.
MTE is an easy-to-use security module with a simple API that handles as much cryptographic functionality as possible for the user. Cryptography is complicated, but MTE wraps those complications in easy-to-use toolkits for web, mobile, and IoT environments. MTE’s implementation helpers and extensions for standard software tools further reduce the implementation effort. MTE often only takes a few hours and a few lines of code to get up and running in an existing application.
It is time to look at data security differently. It is unwise to trust external sources to secure an enterprise’s most valuable asset, data. It is often hard to know or even guarantee that third-party software is not using inherently bad practices or standards. The fact that RSA, a 46-year-old technology, is still so prevalent in the software offerings illustrates that very point. It also provides insight into the growing number of attacks and increasing amount of data stolen year after year. This increase in data compromise is forcing regulatory bodies and insurance companies to hold enterprises financially responsible for these leaks, even though it may not directly be the enterprises’ fault. It is time that enterprises remove their heads from the sand and take control over data security by adding a layer that keeps data protected, from creation to use, no matter what.
For more information, reach out to the Eclypses team: [email protected].


