
With a vast majority of the population using mobile phones on a daily basis and relying heavily on them, it would be devastating for a hacker to gain access to these devices and steal sensitive data.
It’s important to stay ahead of cybercriminals. One major step in doing that is through education. Learning about these attacks and taking the proper steps to implement best practices will help ensure you are protected against potential cyber-attacks.
SIM Swapping and Cloning Attacks
Cybercriminals are using SIM swapping and cloning attacks to access sensitive information. SIM swapping, also called a SIM hijacking attack, happens when someone convinces your mobile carrier to port your phone number over to their SIM card. The person is then able to access your most sensitive accounts/data by completing mobile text 2FA (two-factor authentication) checks.
Cloning attacks are a bit more sophisticated but have the same goal as SIM swapping. Cybercriminals use smart card copying software to create a copy of the real SIM card, which therefore gives access to the victim’s IMSI (international mobile subscriber identity) and master encryption key.
Cybercriminals want your SIM cards so they can access account information, financial information, and PII (personal identifiable information). Once the hacker has a copy of your SIM card, they can use this in a device to control access to the victim’s text, phone calls and location.
A few ways to tell if you have had your SIM card cloned:
- You are no longer receiving text messages or receiving phone calls.
- There are numbers on your account that you do not recognize.
- You are instructed to restart your phone.
- When using a location tracker, it appears your device is in a different location.
- You are locked out of your accounts.
FBI Issues Public Service Announcement
In early 2022, the FBI noticed a surge in SIM swapping attacks and issued a public service announcement, stating the agency received 1,611 SIM-swapping complaints in 2021 and estimates the attacks stole $68 million from victims. Alarmingly, this was a huge increase from previous years.
In their public notice, the FBI urges mobile carriers to educate employees and conduct training sessions on SIM swapping, and carefully inspect incoming email addresses containing official correspondence for slight changes that can make fraudulent addresses appear legitimate and appear to be actual clients.
A Data Protection Solution for SIM Swapping and Cloning Attacks
To prevent SIM swapping, implementing Eclypses MTE Technology helps verify each endpoint connection by putting in place a unique MTE relationship with the physical device and the server it’s trying to communicate with.
For example, during the registration of an application the user is setting up the application (signing in, registering their device, etc.) During this process the app could have the user move a cursor around the screen with their finger. By having the user move their finger around the screen in a random motion, collecting the coordinates of the movements, and then adding them all together – a random, non-replicable, number is created. This number can then be fed into the instantiation of the MTE as part of the seed value. By having a multipart seed value and this random number as part of that value, it makes it nearly impossible for a cybercriminal to hack. The random number will be shared between that specific instance of the app and server, setting up a unique relationship between the two. This number is single-use and will be instantly obsolete after MTE instantiation is complete. This eliminates the ability for someone to discover the value and compromise the communication. With this process in place, the user could give a cybercriminal their username, password, and two-factor authentication code and the criminal would still not be able to log into an app from another device.
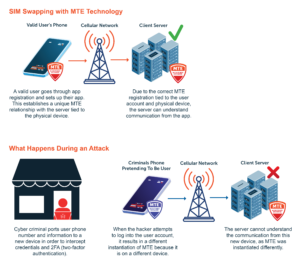
The most crucial part of staying ahead is through education and implementing best practices. In today’s ever-cyber landscape, it is important for individuals and companies to take cyber security seriously to create a safer digital environment for all.
Previously published in Top Cyber News Magazine on Linkedin.


