Quantum computer attacks could soon jeopardize the digital world, putting your online security, privacy and data at risk. As it stands, quantum-resistant security is one of the only things capable of stopping them.
What Is Quantum-Resistant Security?
Quantum-resistant — also known as post-quantum — security involves the development of cryptographic algorithms to protect the digital world from advanced cyber attacks. It’s a defense against theoretical encryption-breaking efforts from advanced computers.
Quantum-resistant security aims to future-proof the digital world against theoretical — but highly likely — threats. You will only stay safe if you have a cryptographic algorithm that can withstand advanced computing attacks.
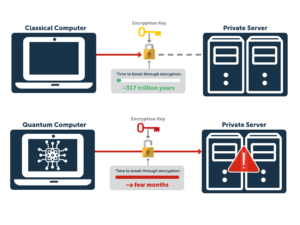
Where a classical computer would take roughly 317 trillion years to break a single encryption key, its quantum counterpart only needs a few months. While these machines only exist in highly controlled environments for now, security experts worldwide believe they will soon become standard.
How Is It Different from Regular Security Methods?
Quantum computers can solve complex calculations unbelievably quickly, which is concerning given that most encryption relies on mathematical formulas. Since these machines have incredible processing power, traditional security strategies will be ineffective against them.
Regular security methods protect encryption by using access limitation, routine updates and secure secret key storage. Frankly, attackers can escalate privileges, replicate keys and rapidly break code if they have a quantum computer. As you can see, the traditional approaches simply won’t work anymore.
If an attacker uses quantum computing to break encryption, you probably won’t be able to stop them with traditional strategies. Considering only 44% of security teams feel they can consistently patch vulnerabilities as they come up, there’s no realistic way for them to respond to advanced decryption attacks.
On the other hand, quantum-resistant security is proactive. It gives you a hand-crafted, purpose-built defense against these attacks. The powerful cryptographic algorithms rely on complex mathematical formulas and unfathomably large numbers no existing technology — quantum computers included — can solve. In reality, it’s the only reliable protection you could use.
How Quantum-Resistant Security Works
Cryptographic algorithms encrypt data, making it readable only to those with secret keys or access privileges. Usually, decryption is borderline impossible because their foundational mathematical functions are far too complex to decipher or crack.
Since the complexity of the mathematics behind these algorithms makes decryption an intensive, lengthy process, you and your data usually remain safe. However, this assumption relies on attackers using classical computers. Needless to say, the formidable processing power of quantum computing is an entirely separate story.
With quantum computers, attackers can bypass standard encryptions using rapid calculations. Since a lengthy number sequence is foundational for most cryptographic algorithms, they only need a machine capable of quickly crunching numbers. In the past, this strategy wasn’t feasible because it would take trillions of years. Even though it’s still somewhat theoretical, it’s much more possible now.
Why Is Quantum-Resistant Security Necessary?
The digital world basically operates on cryptographic algorithms — data storage, information transfers, communications and system access keys use them to stay secure. Essentially, they’re foundational to your online privacy and security. Naturally, quantum computer attacks can easily break them.
This new decryption strategy could make data theft, communication interception, authentication spoofing and key imitation a walk in the park for any attacker. Truthfully, it seems quantum-resistant security is your only hope to keep your data and online behavior secure if these kinds of attacks become common.
Fortunately, many agencies know the implications and are working to create defenses. For instance, the NIST selected its first four cryptographic algorithms in 2022 and hopes to finalize their development by 2026. These specific examples use hash functions and lattice structures, which are mathematical functions capable of resisting a quantum computer attack.
Innovative data security solutions, like Eclypses MTE Technology, combine the use of clever, future-resistant techniques with cryptographic algorithms written in-house. These solutions demonstrate quantum resistance and undergo rigorous testing in accordance with the NIST framework.
The State of Quantum Decryption Methods
Most theoretical attacks rely on Shor’s algorithm — a quantum algorithm for finding prime factors — because it can factor large numbers. In response, security and government agencies like the National Institute of Standards and Technology (NIST) base all of their cryptographic defenses on it.
In an unexpected turn, a professor at New York University proposed a new algorithm capable of decrypting faster and more efficiently than Shor’s. It can function on a smaller quantum computer as well, meaning the digital world is one step closer to widespread attacks.
No one had made a single advancement on Shor’s algorithm in the three decades since its inception, so the development surprised many. It has tremendous implications for the state of quantum-resistant security. On a positive note, you will likely see massive leaps in this technology within your lifetime.
The Future of Quantum Computer Attacks
Even though quantum attacks are still somewhat theoretical, considering these computers are rare and absurdly expensive, high-profile criminal organizations and foreign governments could easily carry them out. Admittedly, quantum-resistant security may be one of the few ways to stay safe online in such an advanced digital world.
Written by: Zachary Amos, Contributor


