
Cybersecurity is in a constant state of evolution, adapting to new technological advancements while cybercriminals seize new opportunities. In order to keep up with these growing threats, it is crucial for security measures to keep pace with these changes. One significant shift that demands attention is mobile app security.
With rapid digitization and increased hybrid work, mobile devices have assumed a more prominent role in both personal and business environments. As a result, mobile apps have become increasingly attractive targets for cybercriminals. Given these evolving circumstances, enhancing app security is of utmost importance. In this article, we outline five important improvements that will be necessary for mobile app security.
Heightened Security Standards
The increasing number of cybercrimes has exposed the inadequacy of many existing security practices, particularly in mobile applications. As awareness increases, it is beginning to drive public opinion towards demanding stronger security measures.
To protect themselves against potential risk, businesses are more likely to require more comprehensive proof of security before partnering with or purchasing apps for their operations. Similarly, consumers will be quick to abandon apps that experience breaches or have significant vulnerabilities that are widely publicized. As the demands for more reliable security increase, developers will be expected to prioritize security over shorter release deadlines and extensive features.

While maintaining a good reputation with consumers and businesses is key for developers on the financial front, these security standards may soon become a matter of legal compliance as well. Data protection regulations are rising, and developers may face substantial fines and other legal consequences for failing to adopt more secure practices and technologies.
Eclypses MTE technology represents the next generation of security. It not only protects data from present attacks but also guards against future threats. By leveraging this technology, data security is isolated, eliminating reliance on elements beyond the app’s control and safeguarding against zero-day exploits, malware, and man-in-the-middle attacks.
Proactive Security Measures
The pursuit of heightened security will drive app developers to incorporate cybersecurity throughout the entire development process, rather than treating it as an add-on. To effectively defend against emerging mobile threats, developers must ensure security from the outset. This entails embracing DevSecOps principles that transform tools, cultures, and processes to make security a shared and central responsibility.
Reactive approaches to security are simply not working anymore as cybercrime grows more sophisticated, and the costs of data breaches skyrocket. Developers must employ automated vulnerability management tools to comprehend their risk landscape and implement necessary changes before criminals exploit vulnerabilities. Penetration testing should also be integrated as a regular part of the development process, rather than being treated as a final step conducted on the finished product.
Eclypses’ MTE technology takes a proactive approach to data security by securing data as soon as it is created in the application, protecting the data from endpoint-to-endpoint. This level of security takes into account:
- The vulnerability and compromise of app users’ devices
- The discovery of zero-day vulnerabilities in the operating system (OS) and applications
- The risk of a device being connected to an insecure network
- The lack of proper IT security training for app users
- The absence of device and application updates
- MTE eliminates replay attacks and other man-in-the-middle (MITM) attacks, providing robust and proactive security.
Reducing Dependency on Single Points
Another significant trend that will shape mobile app security in the future is the growing scrutiny of single dependencies. Mobile apps, often characterized by their simplicity and expedited development, tend to have a higher occurrence of single points of failure. As attacks targeting these apps become more prevalent, developers must transition away from such dependencies to minimize potential damage.
While single dependencies may streamline development, the associated risks are too great. Even features like single sign-on, which are generally more secure than conventional login methods, can fall prey to bugs that allow attackers to easily breach them through brute-force methods. Apps should incorporate multiple layers of security to prevent a single vulnerability from compromising the entire service.
Mitigating these dependencies necessitates regular testing and longer development timelines. Although some businesses may find this prospect less favorable, these steps ultimately reduce the impact of breaches, resulting in long-term cost savings.
Eclypses’ MTE technology is a compiled library that operates independently, ensuring flawless functionality irrespective of external changes. This technology also preserves data security even if other dependencies within the application become compromised.
Enhanced Security for Over-the-Air (OTA) Updates
Mobile apps already undergo regular security updates, but in the near future, there will most likely be increased scrutiny on the integrity of over-the-air (OTA) updates. Events, such as the SolarWinds hack, have underscored the need for improved verification methods for OTA updates. Without proper safeguards, attackers can exploit OTA updates to distribute malicious code to thousands of devices.
Securing OTA updates begins with encrypting and authenticating them. Employing state-of-the-art encryption standards prevents man-in-the-middle attacks, while verification tools like cryptography ensure that updates originate from trusted sources before installation.
Mobile device manufacturers bear responsibility for ensuring these kinds of security measures are implemented. These companies should utilize cryptography, encryption, and similar technologies for all downloads within their app stores, while refusing to host apps that fail to comply with these standards.
Manufacturers can take OTA update security even further by utilizing MTE technology to fragment OTA updates into multiple pieces, each with its unique random encryption key. This approach renders the theft or tampering of OTA updates impossible and guarantees the authenticity of each update.
Security Beyond the App
Mobile app security will extend beyond the confines of the application itself. Developers striving to meet the highest cybersecurity standards must recognize that vulnerabilities within the software supply chain or the development process can compromise an app’s security even before its launch.
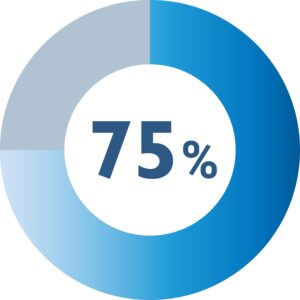
Software supply chain vulnerabilities are alarmingly prevalent. A late 2022 study revealed that over three-quarters of the apps analyzed contained AWS access tokens, effectively granting attackers access to private AWS servers. Trust in the software supply chain is often granted too readily and re-evaluated too infrequently. Continuous monitoring for new threats, even within previously trusted tools, should be an essential aspect of app security. Developers must acknowledge the prevalence of these risks and verify the security of their tools before and during their usage.
Mobile app security must ensure the protection of the entire development environment. This entails employing safer tools, scrutinizing third-party vulnerabilities, holding partners to higher standards, and implementing restrictions to minimize potential supply chain risks.
MTE technology transcends mobile security and enables consistent data security throughout an entire enterprise. It ensures that data remains secure and immutable regardless of its travel path. MTE also guarantees data security, regardless of the user’s cybersecurity practices, the network used, or the level of device compromise. It addresses vulnerabilities that were previously considered unaddressable.
As mobile applications continue to play a central role in everyday life and business operations, the security of these programs becomes increasingly critical.
The five trends will shape app development and security in the near future. As more developers embrace these shifts, apps will become safer, providing enhanced protection for businesses and consumers alike in the face of proliferating threats.
To learn more, contact the Eclypses team here.


