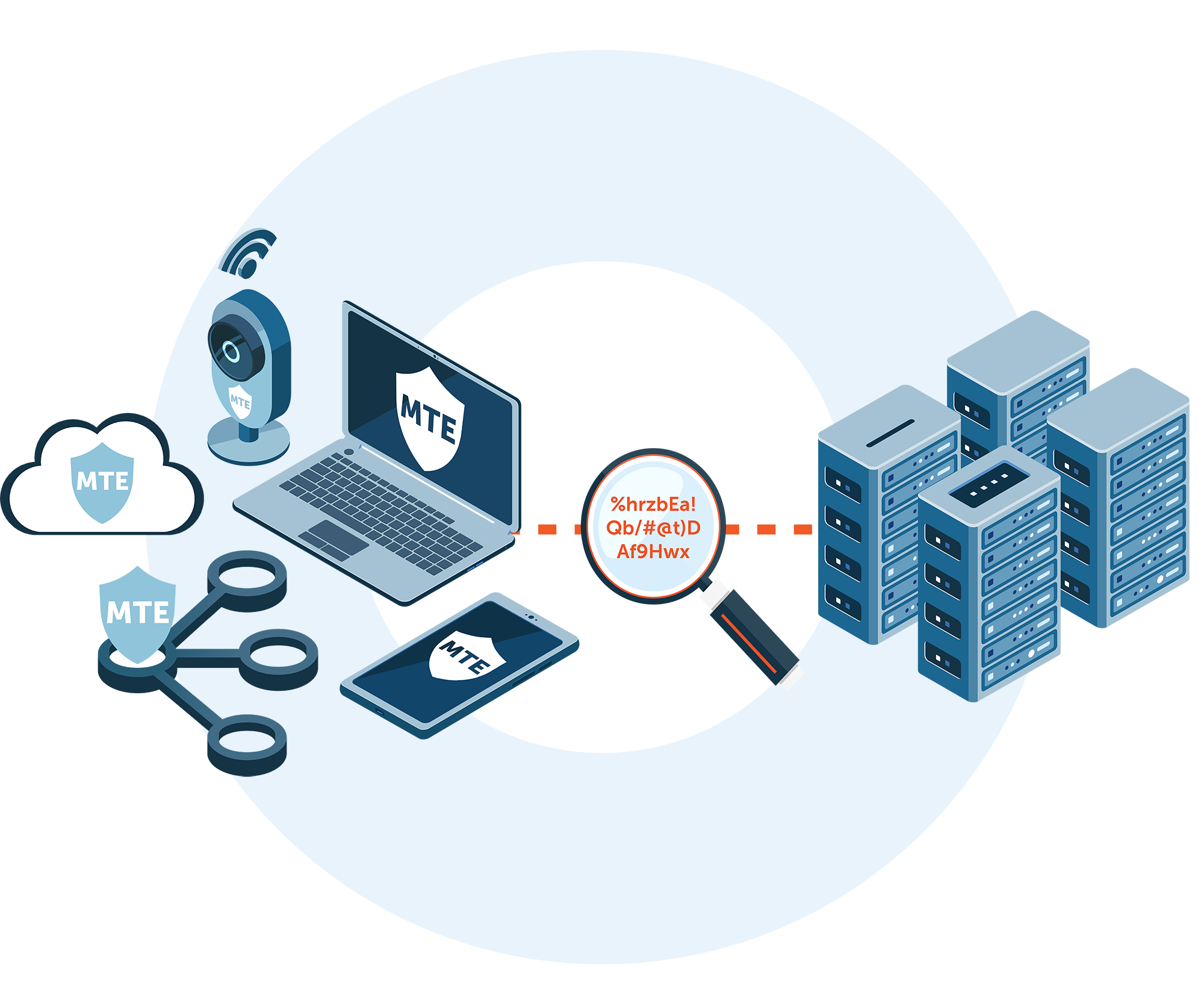
How it Works
MTE technology is a data security solution providing application-level security through our MTE toolkits.
MTE generates instantly obsolete, meaningless, random streams of values that can be used to replace any form of data transmitted between endpoints or can be utilized as single use encryption keys.
Why MTE Technology?
Cyber security organizations have one goal: to keep cyber criminals out, which often means their solution is focused on securing the tunnel, not the actual data.
Why our technology is different
Utilizing our Eclypses Cryptographic Library (ECL), our patented MTE technology replaces your data with instantly obsolete random streams of values and restores it on the other side. By securing at the application level, MTE technology:
- Verifies each endpoint connection
- Requires no change to the user experience
- Minimal impact on system resources
- Secures data inside the application
- Allows you to stop trusting the operating system and communication protocol
What are modern zero-day attacks?
Modern zero-day hacking attacks include attacks at the operating system (OS) which include escalated privilege attacks, compromised credentials, and malicious/rouge applications that can capture your information. These attacks can also include your credentials where secrets are passed between client and server that could be intercepted and do not have endpoint verification. TLS also has the potential for a zero-day attack as it relies on known methods and protocols, is susceptible to replay/certificate hijacking, is zero-knowledge/session-based, and relies on the operating system.
Eclypses Security Approach | A Layered Approach
ECL (Eclypses Cryptographic Library): FIPS 140-3 conformance tested and currently awaiting certification, cryptographic library that provides consistent security for all offerings across all platforms
MTE (MicroToken Exchange): Patented technology that uses ECL to randomize and replace data with random streams of values
MKE (Managed Key Encryption): Uses ECL to randomly replace and encrypt data with single use encryption keys generated by MTE
SDR (Secure Data Replacement): Uses MKE to uniquely encrypt each piece of data that is stored by your application
External Security with MTE and CDP (Customer Data Protection)
Customer Data Protection:
- Application-level MDM style protection for your customer’s data
- Creates redundancy in security with a multi-layer approach
- Reduces your existing attack surface
- MTE not only protects the customer, but it also protects your business from problems customers bring in
Be Proactive – Get Ahead of the Hacks:
- MTE counts on customer devices being vulnerable and compromised
- MTE counts on zero-days being found in OS & applications
- MTE counts on customers not being trained in IT security
- MTE counts on devices and apps not being updated
- MTE eliminates replay and other man-in-the-middle attacks

Protect against targeted attacks that happen at the application level.

Mobile Application Security

Endpoint Verification

Zero Trust with Full Knowledge

Application Level Security

Event-Driven Application Security

Website Security