
Your data is being shoplifted. While ransomware attacks dominate news headlines, a patient/organized enemy is reaping the rewards one vulnerability at a time.
These zero-day exploits, the undisclosed software vulnerabilities used to attack critical systems, might be the most valuable asset a bad actor can have. This year alone, cybersecurity experts have recorded the highest number ever.
Thanks to the tireless cybersecurity professionals who track zero-days, such as the Zero-Day Tracking Project, we have recorded more than double the amount of zero-day exploits in 2021 (83) versus the previous year (36). While the number is concerning on its own, the affected systems, the types of vulnerabilities, and the presumed unreported numbers may be worse.
At a quick glance, in 2021:
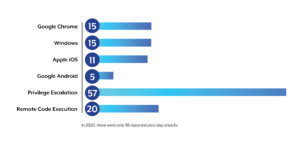
Even though the reasons for the increase vary, many cyber criminals seem motivated financially by the growth of exploit-as-a-service. What was once niche and prohibitively expensive has become easier and more sophisticated in recent years and some exploits are worth thousands in private bounties. An article posted by Bleeping Computer details the current big money bounty economy for attacks on specific targets.
The addition of readily available, open-source tools eliminates many barriers to entry and the participation of nation-state-linked and well-funded groups acting according to political objectives adds to the overwhelming prospect of preventing the fallout. Meanwhile, innocent businesses and customers are left holding the bill.
For companies with compliance and security requirements, prevention is ideal but often impossible. The reality is that while the exploit is unpatched, there is little a business or consumer can do about it. If an operating system has allowed escalated privileges on a customer’s device, even though a company has designed its software, mobile application, or website correctly and conforming to best practices, the data can be taken and used maliciously. At the end of the day, data monitoring, while essential for a zero-trust architecture, tends to be reactive rather than proactive.
Since traditional security monitoring is limited and patching can take days, this problem may seem like a losing battle. Fortunately, businesses may find the solution to harden their applications is simple – don’t trust the operating system.
Eclypses MTE technology is an application-level technology specifically designed to secure application data before it hits the operating system, the network, or the transport layer. The patented use of Eclypses cryptographic modules allows businesses to control their application data without the reliance on uncontrolled and vulnerable systems. In addition, MTE includes endpoint verification, key management, and unique protection to most man-in-the-middle attacks using toolkits specifically designed for the use case.
If traditional security is unable to protect against the shifting world of modern vulnerabilities, it may be time to adopt application-level security as a new best practice. When an exploit results in hours and dollars spent in repair, the loss of customer data and an undeserved loss of reputation, the time to act is now. In the (likely) event we wake tomorrow with the discovery of a new zero-day, each day spent waiting is another day our data is being shoplifted. To learn more about protecting your firm for the future, contact us today.
Written by: Joe Jeanjaquet, Eclypses Senior Director of Applied Technologies


